Our Products
Comprehensive industrial automation solutions for global industries
Contact us
If you are interested in our products and want to know more details,please Contact us,we will reply you as soon as we can.

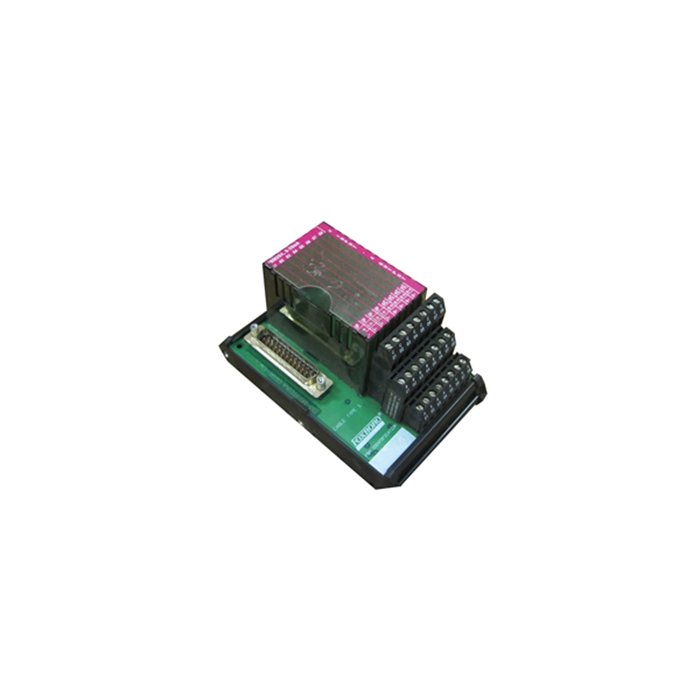




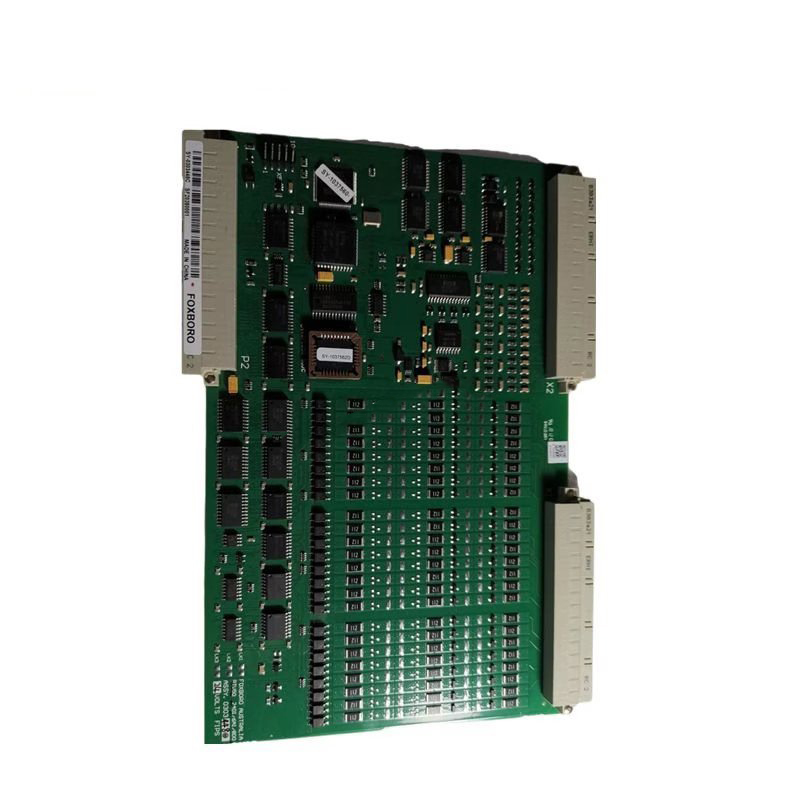




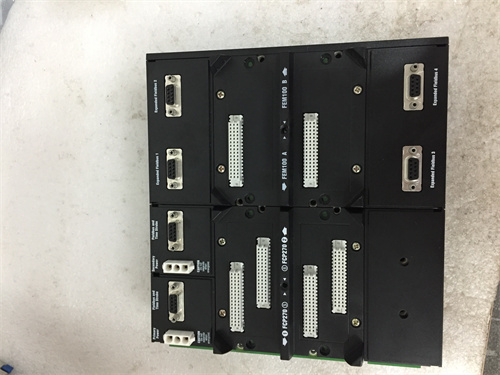
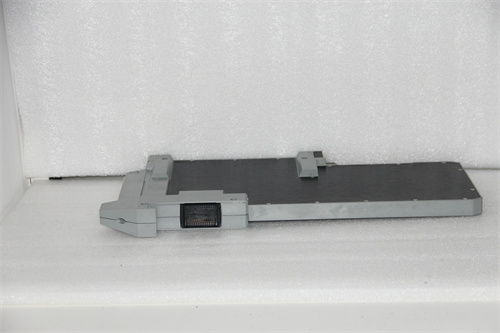
Foxboro FBM203 P0914SV Avoiding Code Injection Controller
Module Number:FBM203 P0914SV
Product status:Discontinued
Delivery time:In stock
Sales country:All over the world
Product situation:Brandnew , one year warranty
Product Description
The best way to avoid code FBM203 is through design. If you can use a language that will never have vulnerabilities, then this is best because your code is immune to all attacks during construction; Alternatively, you can design code to prohibit interfaces that may cause these issues.
Unfortunately, in embedded systems, these choices are not always feasible. Even though C is a dangerous language full of vulnerabilities, it is still the preferred language for many organizational structures. Given this, developers should be aware of other methods to avoid code injection.

Two golden FBM203 to follow to prevent code injection vulnerabilities:
·If you can avoid it, try not to compile data like code;
·If you are unable to avoid it, please make sure to verify if the data is good before using it.
To avoid loopholes in format strings, the first of these rules is the most appropriate; You can write the following code:
Printf (“% s”, str);
In this way, the content of FBM203 is only considered as data. This is the least brainy way, as long as you can find all the places where this kind of modification should be made. But this can be tricky for large programs, especially for third-party code libraries.


Foxboro FBM203 P0914SV Avoiding Code Injection Controller
Module Number:FBM203 P0914SV
Product status:Discontinued
Delivery time:In stock
Sales country:All over the world
Product situation:Brandnew , one year warranty
Product Description
The best way to avoid code FBM203 is through design. If you can use a language that will never have vulnerabilities, then this is best because your code is immune to all attacks during construction; Alternatively, you can design code to prohibit interfaces that may cause these issues.
Unfortunately, in embedded systems, these choices are not always feasible. Even though C is a dangerous language full of vulnerabilities, it is still the preferred language for many organizational structures. Given this, developers should be aware of other methods to avoid code injection.

Two golden FBM203 to follow to prevent code injection vulnerabilities:
·If you can avoid it, try not to compile data like code;
·If you are unable to avoid it, please make sure to verify if the data is good before using it.
To avoid loopholes in format strings, the first of these rules is the most appropriate; You can write the following code:
Printf (“% s”, str);
In this way, the content of FBM203 is only considered as data. This is the least brainy way, as long as you can find all the places where this kind of modification should be made. But this can be tricky for large programs, especially for third-party code libraries.
Need a Custom Automation Solution?
Our team of experts can design and implement a tailored automation system to meet your specific requirements.


 Loading comments...
Loading comments...